5 Burp Suite Tips & Tricks
If you're using Burp Suite, you have to know these 5 Tips and Tricks for the best usage when bug bounty hunting or penetration testing.

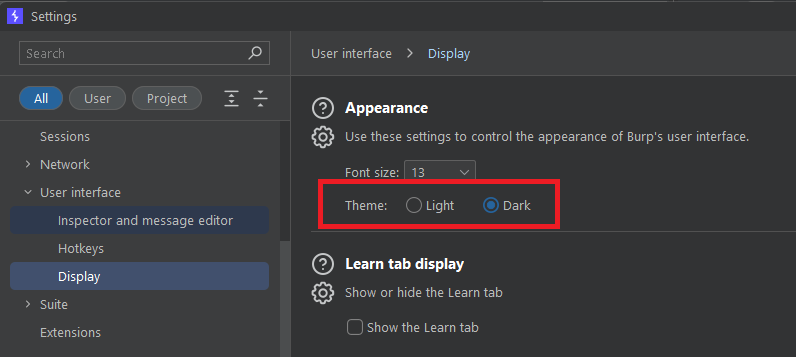
Dark Mode
The very first thing you need to do with Burp Suite is enable dark mode. Save yourself the headache, because if you're a serious hunter, you'll be using Burp Suite for hours. Go to Settings -> User Interface -> Display -> Theme: Dark.
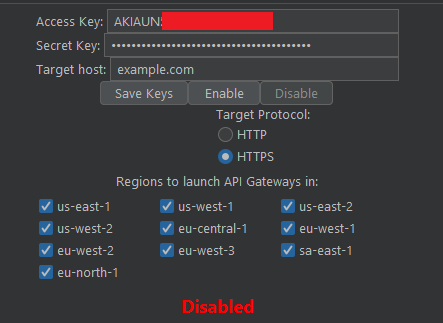
Rotate Your IP Address
Before sending off any traffic to your targets, you may want to ensure that your own IP Address is hidden. This is so you don't end up getting your home IP Address banned on Akamai, Cloudflare of any of the many WAFs.
You can do that using IP Rotate from the Burp Suite Extensions tab. Simply input your AWS access keys and the extension will take care of hiding your IP Address.
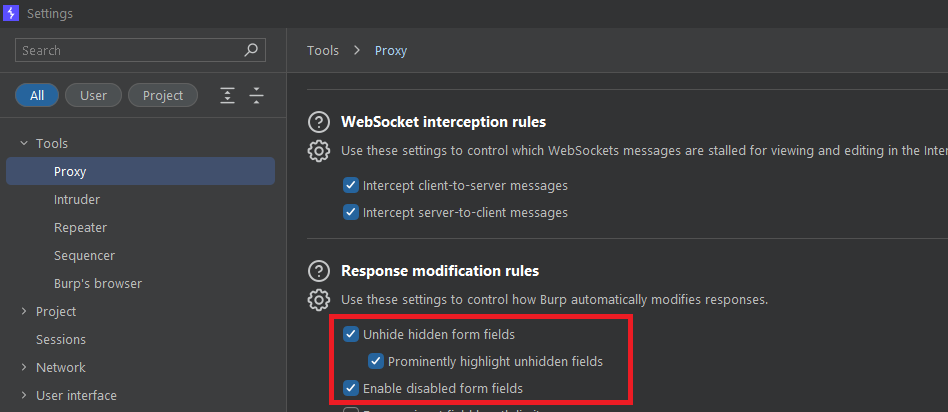
Flipping Forms and Boolean
Web applications typically implement form fields that are hidden or disabled, waiting for a condition to be met for them to enable. Hidden form fields are used to store tokens, like CSRF tokens and other potentially sensitive data. Disabled forms may be used for functionality that should be used when certain conditions are met in the web application.
Burp Suite has the ability to unhide and enable these forms. You can do this by going to Settings -> Tools -> Proxy -> Response Modification Rules.
You may see the related form parameters in HTTP Responses anyway. But using this Burp Suite feature may be of benefit as it will visually show the data and forms on the web application, and may visualise logic flaws that you may otherwise miss.
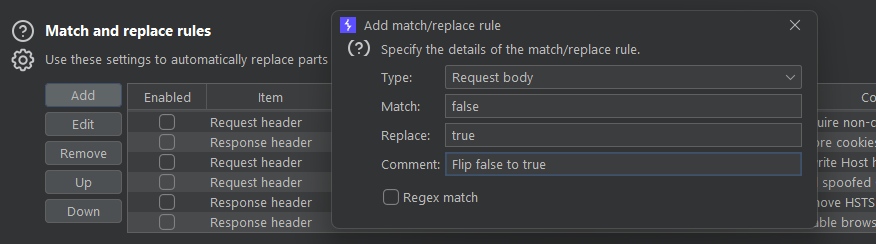
Another similar tip to try is switching false to true and vice-versa. This may present logic flaws and in some cases, could even lead to privilege escalation. Go to Settings -> Tools -> Proxy -> Match and Replace Rules:
Using Multiple Proxies for Tooling
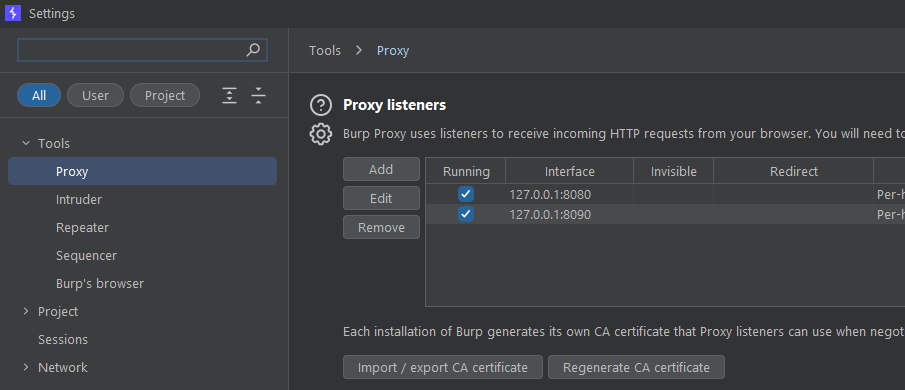
Typically, you likely only use one Burp proxy, which is 127.0.0.1:8080. Go to Settings -> Tools -> Proxy -> Proxy Listeners and create one or more extra proxy for your tooling. For example, create a listener on port 8090 and use that to proxy SQLMAP, which creates a lot of requests and can swamp your logger.
By using another port, it is easy to then filter out port 8090 or compare the differences in response between the two ports.
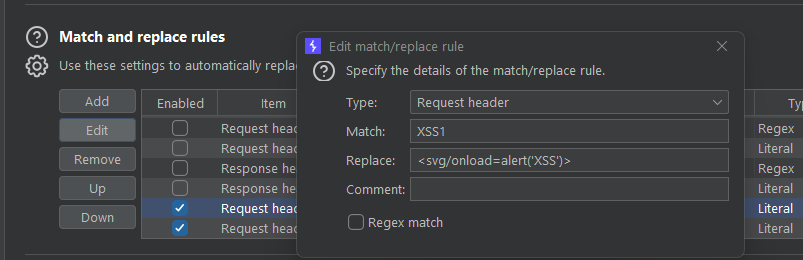
Match and Replace Injections
Having to keep going to your notes or manually typing out injection payloads into web parameters and web forms is very long. But, bot with Burps Match and Replace feature! Go to Settings -> Tools -> Proxy -> Match and Replace Rules.
You can set it so XSS1 auto changes into your favourite XSS payload and you can do this for all the payloads you want. Then, rather than typing out each payload, just type in XSS1 into any parameters you want to test.