cPanel CVE-2023-29489
CVE-2023-29489 is a security vulnerability in cPanel that can allow an attacker to execute arbitrary code and effect users of the application via XSS. To protect against this, it is important to keep software up to date and use additional security measures where possible.

Recently, a security vulnerability known as CVE-2023-29489 was discovered which affects certain versions of cPanel.
What is CVE-2023-29489? (Simplified)
This vulnerability has the potential to affect users of cPanel and force them to conduct unintended actions. This can include stealing personal or sensitive data, downloading malware, changing the websites hosted by cPanel or even using the victims computer as part of a larger attack on another organization.
The reason this vulnerability is so concerning is that it can be exploited without any authentication, meaning an attacker doesn't need to be logged into the cPanel instance to exploit this issue. An attacker would simply have to trick a user into clicking a URL.
To mitigate, CVE-2023-29489, make sure you're running up-to-date cPanel on your servers. Any of the below cPanel versions will prevent this issue from being exploited:
- 11.109.9999.116
- 11.108.0.13
- 11.106.0.18
- 11.102.0.31
What is CVE-2023-28252? (Detailed)
Well, there's no need to reinvent the wheel here when AssetNote have written about this so well already. Big shoutout to AssetNote for finding this issue.
Finding vulnerable cPanels
Ethical Hackers and Bug Bounty extraordinaires will be asking how they can find affected cPanels. Well, as we mention in our other blog, the best way to do this is with Nuclei. Don't wait for others to create new exploit templates because you'll be too late, go ahead and make the template yourself based on this CVE!

We haven't made a Nuclei template, but in a very small amount of time (1 minute), we went onto Shodan and looked for the port cPanel runs on, which is 2082:
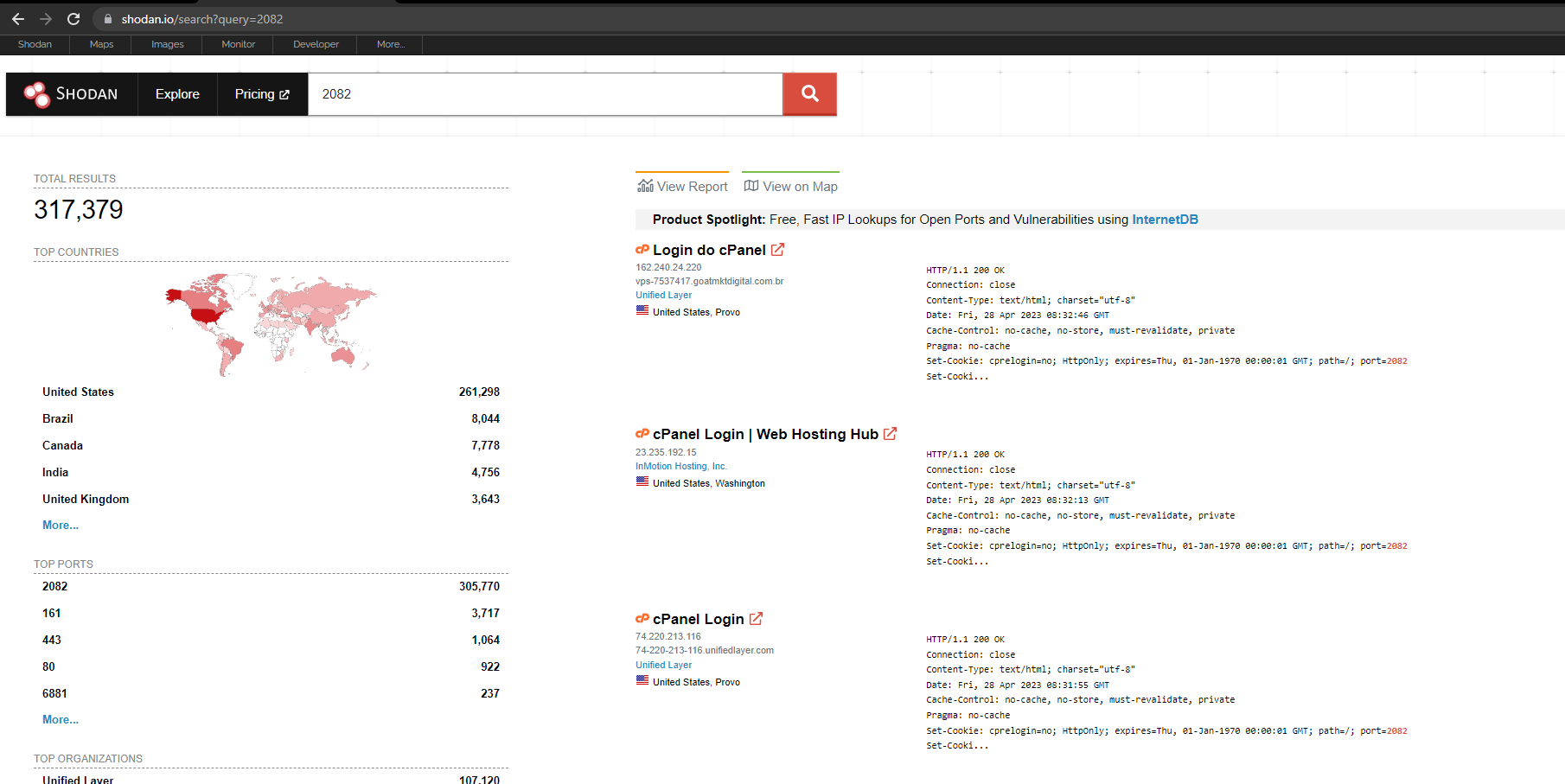
Using the PoC examples given by AssetNote, shown below. We were able to find a vulnerable cPanel instance right away, so it is possible to find them and likely, quite easily:
Proof Of Concept - Exploit Code:
http://example.com/cpanelwebcall/<img%20src=x%20onerror="prompt(1)">aaaaaaaaaaaa

Shodan is just one way to find exposed targets, we talk about other ways in our recon blog:





